|
|
Using DNS to avoid malicious sites
by Chris Taylor
In the
article "The Failure of Antivirus" (Ottawa PC
News, November, 2011), I talked about how there is
no such thing as a safe web site any more. As reported by
the security company Sophos, in 2011, they found 19,000
new malicious URLs per day. Eighty percent of
them were compromised, legitimate web sites.
There are frequent zero-day exploits for vulnerabilities
in common software. A zero-day exploit is one for which
no security patch yet exists.
The bad guys are reverse-engineering security patches to
develop and distribute malware that exploits
vulnerabilities before people get the security patches
installed that fix those vulnerabilities.
Time frames to react are getting shorter and shorter.
Signature file updates in antivirus software is simply
not a complete solution any more. New techniques are
needed to deal with all this bad stuff.
One technique that has been around for years and is now
baked into browsers or available as a plug-in, is to
verify the reputation of a web site before allowing your
browser to render that content of a web site. Here is an
example of how it all works.
Say you want to browse to www.CoolApps.net. The browser
or a plug-in will first check the reputation of the web
site through a trusted service. If it is not known to be
bad, the browser or plug-in will allow the browser to
load the page.
Let's say the reputation service gets word that the site
www.CoolApps.net has been compromised. They might find
out through a report from a user. Or perhaps they have
robots checking sites. As soon as they find out that a
given site now contains malicious content, they can make
a change in their reputation service so that the next
time someone who uses their reputation service tries to
go to the site, a code goes back to the browser to not
load the page. Usually it will cause a warning page to be
displayed indicating the site contains known malicious
content. The user can then decide to over-ride the
warning and go to the site anyway or they can heed the
warning and avoid going to the site.
There was one part in the chain of events above that I
skipped over.
Your browser has no idea about how to get to
www.CoolApps.net. It can only go to an IP address, such
as 24.103.2.12. How does your computer figure out the IP
address to go to? Enter DNS or the Domain Name System.
You type in www.CoolApps.net, your computer queries DNS
to find the IP address and then your browser connects to
the IP address.
What if you could combine DNS with a reputation service?
That's exactly what Symantec has done with Norton DNS
for Home. All you have to do is configure your DNS
settings to point to Norton DNS for Home rather
than the typical configuration where you point to the DNS
server operated by your Internet Service Provider.
Once configured, all DNS queries go through the Norton
DNS for Home server. If the site is not known to be
bad, everything operates as usual. If the site is known
to be bad, you get directed to a page that tells you why
you are being prevented from reaching the site.
More than just malware protection
One of the cool things about Norton DNS for Home
is that Symantec is actually running three DNS services.
The first one blocks sites for security issues –
malware, phishing, scam sites and web proxies. The second
blocks based on security issues as well as pornography.
The third blocks for security, pornography and what
Symantec calls non-family-friendly sites that deal with
mature content, abortion, alcohol, crime, cults, drugs,
gambling, hate, sexual orientation, suicide, tobacco or
violence.
If you have a router that you use to connect multiple
computers to the Internet, Symantec recommends that you
configure the DNS settings in the router to use Norton
DNS for Home. If all computers connecting to the
Internet through your router are set up in the default
configuration, they will point to the router for DNS and
automatically use Norton DNS for Home.
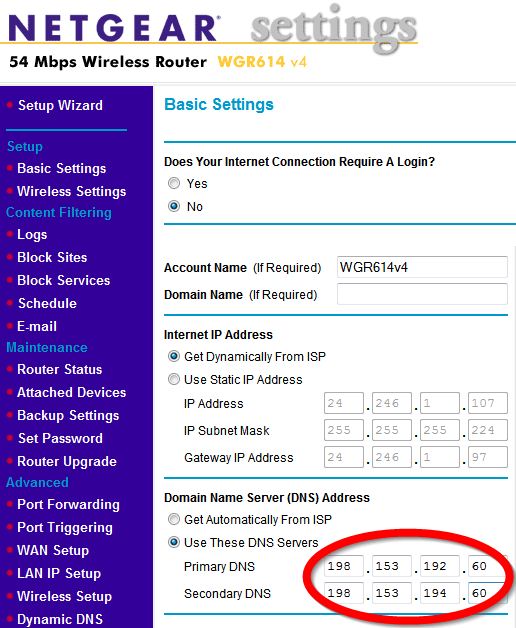
Setting a router to use Norton DNS for Home
If you only want
certain computers to use Norton DNS for Home,
you can easily configure individual computers to use Norton
DNS for Home. Individual computer configuration is
also good when you want to use different levels of
protection for different computers. For example, you
might have your own computer use protection just for
security reasons. On the kids’ computer, you might
go for protection for security, pornography and
non-family friendly.
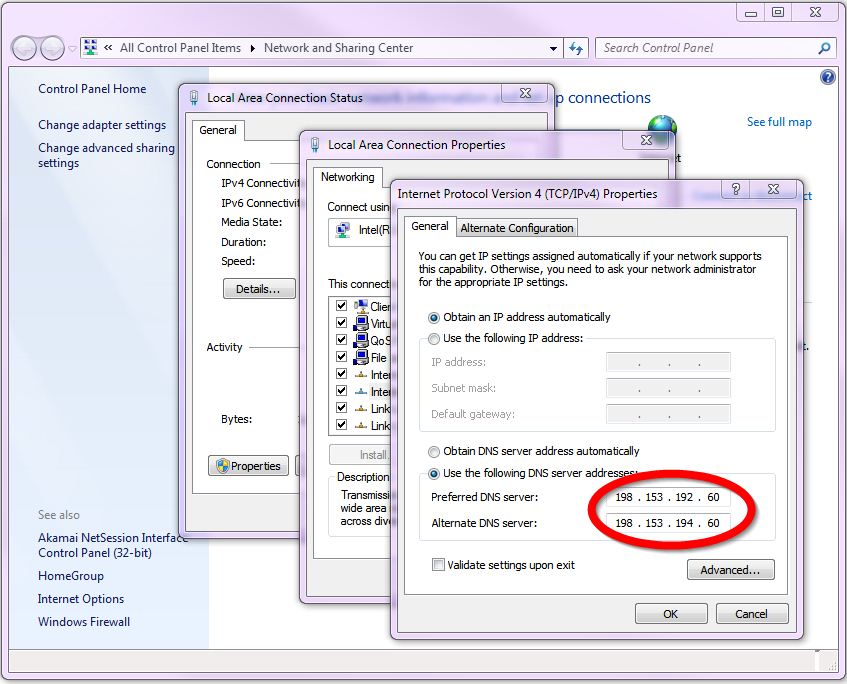
Setting DNS in Windows 7 to use Norton DNS for Home

Norton DNS for Home blocking access to a 'non-family-friendly' web site
While Norton
DNS for Home is only for personal/home use,
Symantec also runs a service for businesses.
To see how to configure your computer to use Norton DNS
for Home, visit their site at https://dns.norton.com/dnsweb/dnsForHome.do
Originally published: May, 2012
top of page
|
Archived Reviews
A-J
K-Q
R-Z
The opinions expressed in these reviews
do not necessarily represent the views of the
Ottawa PC Users' Group or its members.
|